CDNetworks Successfully Mitigated a 1.01 Tbps Ransom DDoS Attack on a Major Software Download Platform
Table of Contents

Executive Summary
-
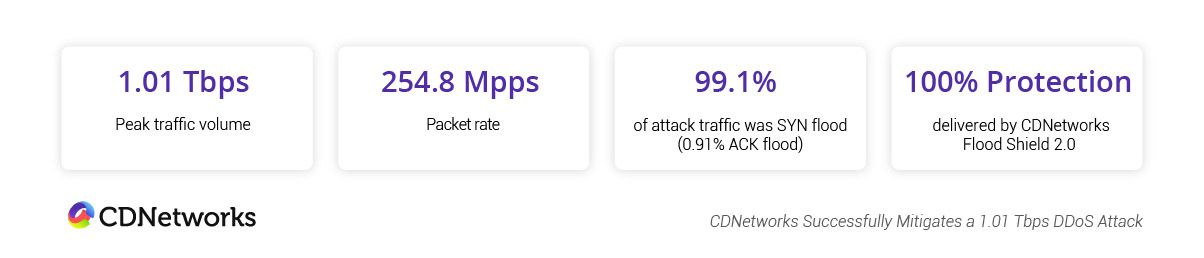
On October 11, 2025, CDNetworks successfully mitigated a large-scale DDoS attack against a major software download platform. The attack peaked at 1.01 Tbps and used a mix of SYN and ACK flood vectors to overwhelm the customer’s origin servers.
-
This attack was part of a broader, organized ransom DDoS (RDDoS) campaign that persisted for over one month. CDNetworks Flood Shield 2.0, our DDoS protection platform, blocked 100% of malicious traffic with no impact to legitimate users.
-
The customer remained fully operational throughout the campaign, experiencing zero downtime.
Anatomy of the Attack
Background
Beginning October 2, 2025, the customer was hit by a series of disruptive DDoS attacks. Not long after, the customer received an extortion email from the attacker (as shown below).
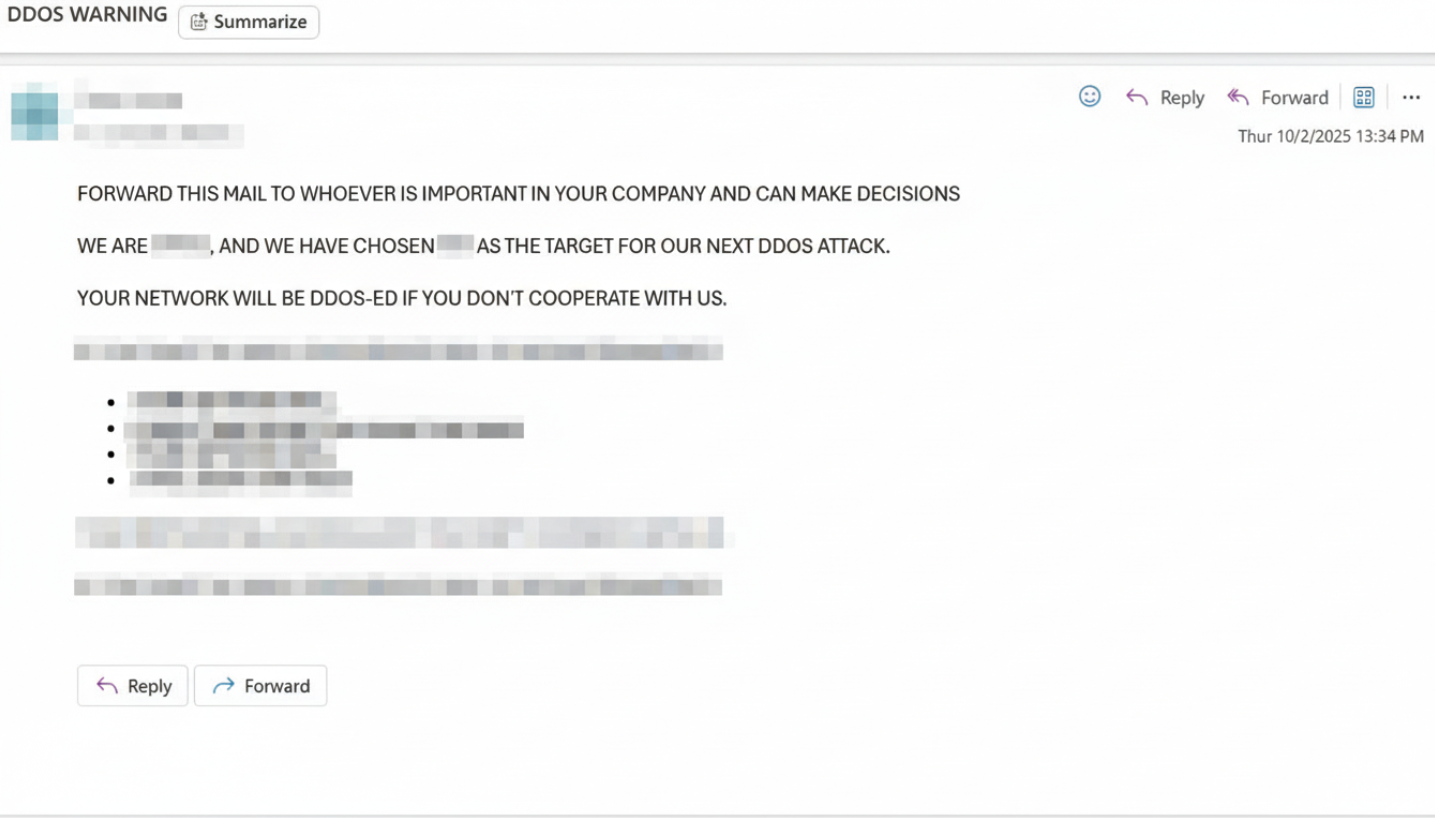
Figure 1. Ransom email received by the customer.
The attack caused the platform’s legitimate traffic to decline to around one-third of its usual levels. The customer turned to CDNetworks to stop the attack in its tracks.
CDNetworks’ Mitigation of the Attack
On October 8, 2025, CDNetworks security operations specialists worked with the customer to activate Flood Shield 2.0, our DDoS protection services.
On October 11, Flood Shield 2.0 mitigated the largest observed peak of the campaign, which reached 1.01 Tbps and consisted primarily of high-volume SYN and ACK flood vectors directed at the customer’s origin servers.
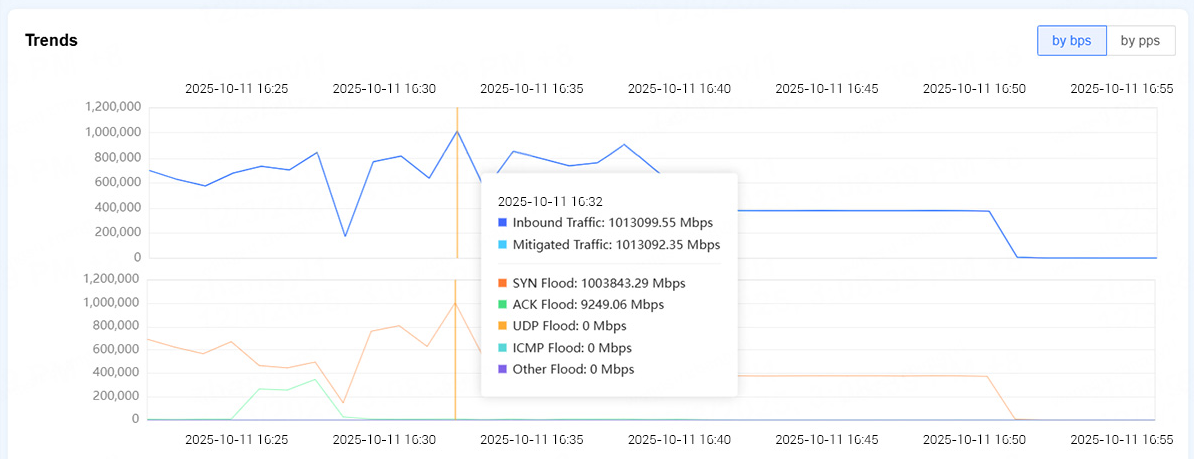
Figure 2. Flood Shield 2.0 automatically mitigated a 1.01 Tbps attack
Backed by CDNetworks’ globally distributed scrubbing centers and 20+ Tbps of mitigation capacity, malicious traffic was identified and filtered in real time. Legitimate user access remained uninterrupted despite the scale of the attack.
The campaign continued for several weeks, as shown in the chart below. All subsequent attempts were mitigated by Flood Shield 2.0, and the campaign ceased on November 8, 2025.
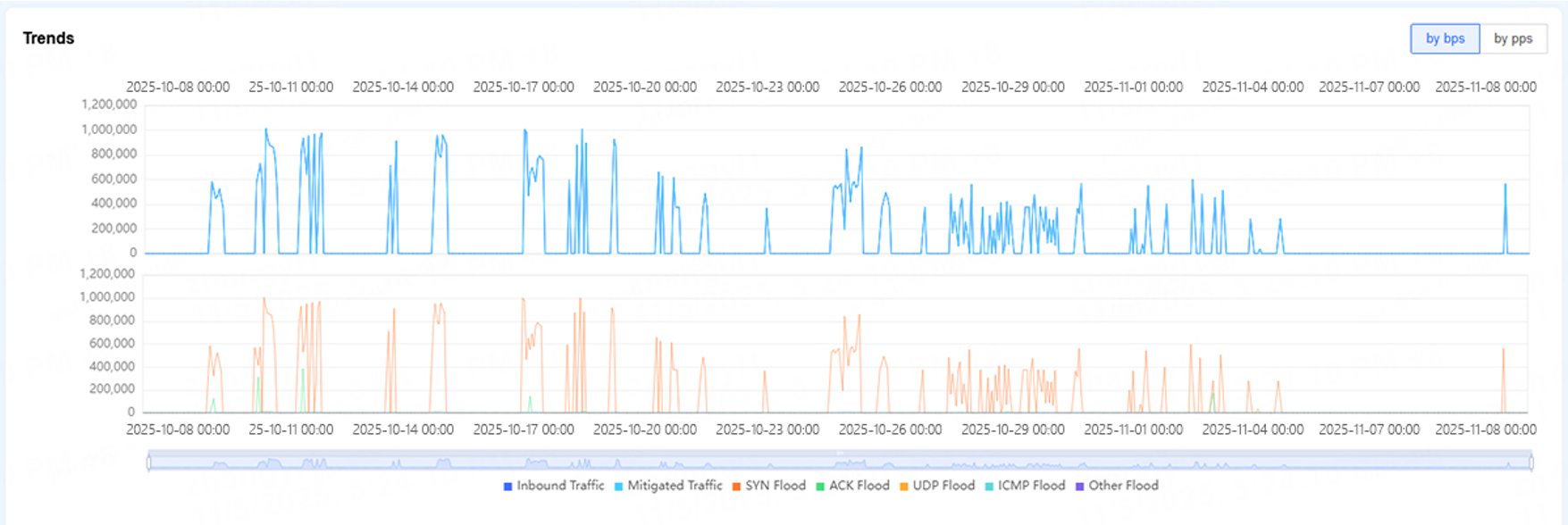
Figure 3. Full attack trend
Key Metrics at a Glance
Industry-wide RDDoS Extortion
This customer’s experience was not an isolated incident. Throughout Q4 2025, we have monitored a repeat of this attack pattern against over 20 organizations in the software-distribution industry, all extorted by the same threat group.
The group followed a predictable pattern: launch high-volume DDoS attacks to disrupt the target organization’s operations, demand payment for grossly overpriced “traffic packages,” and pressure targeted platforms into compliance.
If the target organization refused to cooperate, the attackers threatened to replace legitimate installers with malware-infested versions.
Key Takeaways from This Incident
In recent years, we’ve seen a noticeable surge in Ransom DDoS (RDDoS) attacks, and the pattern behind them is becoming clearer. Attackers are no longer just aiming to overwhelm a target’s network; they are using short, sharp bursts of traffic to create panic and pressure organizations into paying. These incidents often start with small “demo attacks” meant to prove capability before the ransom note even arrives.
But when teams prepare in advance, establish a clear response plan, and have the right mitigation in place, the extortion loses its leverage.
Based on our experience supporting customers through similar incidents, these are the 5 essential steps every organization should keep in mind:
- DO NOT reply to or pay extortion demands — any engagement tends to increase attacker persistence.
- Alert internal security/network teams as early as possible — rapid coordination shortens the window of impact.
- Preserve every signal (threat emails, traffic anomalies, timestamps) — these details matter for attribution, law-enforcement reports, and tuning mitigation.
- Ensure your DDoS protection is already active and tested — in extortion scenarios, the only reliable way to absorb large volumetric surges is through professional mitigation platforms with global scrubbing capacity, such as Flood Shield 2.0.
- Establish a clear incident-response plan and crisis team — define responsibilities and procedures in advance so your team can act decisively during an attack.
Contact us if you’re under attack right now or if you want to strengthen your DDoS protection.
If you want to understand how the broader DDoS landscape is evolving and what indicators to watch for, we break down these patterns in more detail in our latest whitepaper.
It’s a practical resource to help teams benchmark their current defenses and prepare for the next wave of attacks. Download here 👇

More To Explore
Key Cybersecurity Statistics and Emerging Trends for 2026
A data-driven overview of cybersecurity statistics and emerging threats shaping 2026, including AI-driven attacks, DDoS, API exploitation, ransomware, phishing.